Archive:
June 21, 2018 / by Marco / Bundle, Business', deals, design, entrepreneur, Learning, Reinforcement, website

Reinforcement Learning Bundle for $39

KEY FEATURES
A/B testing is used everywhere, from marketing, retail, news feeds, online advertising, and much more. If you’re a data scientist, and you want to tell the rest of the company, “logo A is better than logo B,” you’re going to need numbers and stats to prove it. That’s where A/B testing comes in. In this course, you’ll do traditional A/B testing in order to appreciate its complexity as you elevate towards the Bayesian machine learning way of doing things.
- Access 40 lectures & 3.5 hours of content 24/7
- Improve on traditional A/B testing w/ adaptive methods
- Learn about epsilon-greedy algorithm & improve upon it w/ a similar algorithm called UCB1
- Understand how to use a fully Bayesian approach to A/B testing
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels, but knowledge of calculus, probability, Python, Numpy, Scipy, and Matplotlib is expected
- All code for this course is available for download here, in the directory ab_testing
Compatibility
- Internet required
THE EXPERT
The Lazy Programmer is a data scientist, big data engineer, and full stack software engineer. For his master’s thesis he worked on brain-computer interfaces using machine learning. These assist non-verbal and non-mobile persons to communicate with their family and caregivers.
He has worked in online advertising and digital media as both a data scientist and big data engineer, and built various high-throughput web services around said data. He has created new big data pipelines using Hadoop/Pig/MapReduce, and created machine learning models to predict click-through rate, news feed recommender systems using linear regression, Bayesian Bandits, and collaborative filtering and validated the results using A/B testing.
He has taught undergraduate and graduate students in data science, statistics, machine learning, algorithms, calculus, computer graphics, and physics for students attending universities such as Columbia University, NYU, Humber College, and The New School.
Multiple businesses have benefitted from his web programming expertise. He does all the backend (server), frontend (HTML/JS/CSS), and operations/deployment work. Some of the technologies he has used are: Python, Ruby/Rails, PHP, Bootstrap, jQuery (Javascript), Backbone, and Angular. For storage/databases he has used MySQL, Postgres, Redis, MongoDB, and more.

KEY FEATURES
Variational autoencoders and GANs have been two of the most interesting recent developments in deep learning and machine learning. GAN stands for generative adversarial network, where two neural networks compete with each other. Unsupervised learning means you’re not trying to map input data to targets, you’re just trying to learn the structure of that input data. In this course, you’ll learn the structure of data in order to produce more stuff that resembles the original data.
- Access 41 lectures & 5.5 hours of content 24/7
- Incorporate ideas from Bayesian Machine Learning, Reinforcement Learning, & Game Theory
- Discuss variational autoencoder architecture
- Discover GAN basics
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels, but knowledge of calculus, probability, object-oriented programming, Python, Numpy, linear regression, gradient descent, and how to build a feedforward and convolutional neural network in Theano and TensorFlow is expected
- All code for this course is available for download here, in the directory unsupervised_class3
Compatibility
- Internet required
THE EXPERT
The Lazy Programmer is a data scientist, big data engineer, and full stack software engineer. For his master’s thesis he worked on brain-computer interfaces using machine learning. These assist non-verbal and non-mobile persons to communicate with their family and caregivers.
He has worked in online advertising and digital media as both a data scientist and big data engineer, and built various high-throughput web services around said data. He has created new big data pipelines using Hadoop/Pig/MapReduce, and created machine learning models to predict click-through rate, news feed recommender systems using linear regression, Bayesian Bandits, and collaborative filtering and validated the results using A/B testing.
He has taught undergraduate and graduate students in data science, statistics, machine learning, algorithms, calculus, computer graphics, and physics for students attending universities such as Columbia University, NYU, Humber College, and The New School.
Multiple businesses have benefitted from his web programming expertise. He does all the backend (server), frontend (HTML/JS/CSS), and operations/deployment work. Some of the technologies he has used are: Python, Ruby/Rails, PHP, Bootstrap, jQuery (Javascript), Backbone, and Angular. For storage/databases he has used MySQL, Postgres, Redis, MongoDB, and more.

KEY FEATURES
This course is all about the application of deep learning and neural networks to reinforcement learning. The combination of deep learning with reinforcement learning has led to AlphaGo beating a world champion in the strategy game Go, it has led to self-driving cars, and it has led to machines that can play video games at a superhuman level. Unlike supervised and unsupervised learning algorithms, reinforcement learning agents have an impetus—they want to reach a goal. In this course, you’ll work with more complex environments, specifically, those provided by the OpenAI Gym.
- Access 52 lectures & 5 hours of content 24/7
- Extend your knowledge of temporal difference learning by looking at the TD Lambda algorithm
- Explore a special type of neural network called the RBF network
- Look at the policy gradient method
- Examine Deep Q-Learning
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels, but knowledge of calculus, probability, object-oriented programming, Python, Numpy, linear regression, gradient descent, how to build a feedforward and convolutional neural network in Theano and TensorFlow, Markov Decision Processes, and how to implement Dynamic Programming, Monte Carlo, and Temporal Difference is expected
- All code for this course is available for download here, in the directory rl2
Compatibility
- Internet required
THE EXPERT
The Lazy Programmer is a data scientist, big data engineer, and full stack software engineer. For his master’s thesis he worked on brain-computer interfaces using machine learning. These assist non-verbal and non-mobile persons to communicate with their family and caregivers.
He has worked in online advertising and digital media as both a data scientist and big data engineer, and built various high-throughput web services around said data. He has created new big data pipelines using Hadoop/Pig/MapReduce, and created machine learning models to predict click-through rate, news feed recommender systems using linear regression, Bayesian Bandits, and collaborative filtering and validated the results using A/B testing.
He has taught undergraduate and graduate students in data science, statistics, machine learning, algorithms, calculus, computer graphics, and physics for students attending universities such as Columbia University, NYU, Humber College, and The New School.
Multiple businesses have benefitted from his web programming expertise. He does all the backend (server), frontend (HTML/JS/CSS), and operations/deployment work. Some of the technologies he has used are: Python, Ruby/Rails, PHP, Bootstrap, jQuery (Javascript), Backbone, and Angular. For storage/databases he has used MySQL, Postgres, Redis, MongoDB, and more.

KEY FEATURES
When people talk about artificial intelligence, they usually don’t mean supervised and unsupervised machine learning. These tasks are pretty trivial compared to what we think of AIs doing—playing chess and Go, driving cars, etc. Reinforcement learning has recently become popular for doing all of that and more. Reinforcement learning opens up a whole new world. It’s lead to new and amazing insights both in behavioral psychology and neuroscience. It’s the closest thing we have so far to a true general artificial intelligence, and this course will be your introduction.
- Access 71 lectures & 5.5 hours of content 24/7
- Discuss the multi-armed bandit problem & the explore-exploit dilemma
- Learn ways to calculate means & moving averages and their relationship to stochastic gradient descent
- Explore Markov Decision Processes, Dynamic Programming, Monte Carlo, & Temporal Difference Learning
- Understand approximation methods
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels, but knowledge of calculus, probability, object-oriented programming, Python, Numpy, linear regression, and gradient descent is expected
- All code for this course is available for download here, in the directory rl
Compatibility
- Internet required
THE EXPERT
The Lazy Programmer is a data scientist, big data engineer, and full stack software engineer. For his master’s thesis he worked on brain-computer interfaces using machine learning. These assist non-verbal and non-mobile persons to communicate with their family and caregivers.
He has worked in online advertising and digital media as both a data scientist and big data engineer, and built various high-throughput web services around said data. He has created new big data pipelines using Hadoop/Pig/MapReduce, and created machine learning models to predict click-through rate, news feed recommender systems using linear regression, Bayesian Bandits, and collaborative filtering and validated the results using A/B testing.
He has taught undergraduate and graduate students in data science, statistics, machine learning, algorithms, calculus, computer graphics, and physics for students attending universities such as Columbia University, NYU, Humber College, and The New School.
Multiple businesses have benefitted from his web programming expertise. He does all the backend (server), frontend (HTML/JS/CSS), and operations/deployment work. Some of the technologies he has used are: Python, Ruby/Rails, PHP, Bootstrap, jQuery (Javascript), Backbone, and Angular. For storage/databases he has used MySQL, Postgres, Redis, MongoDB, and more.

Raspberry Pi 3 + Speech Controlled Smart Robot Car Kit for $169

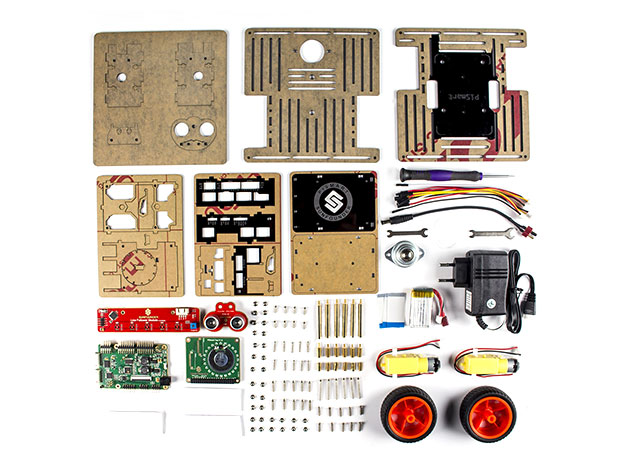
KEY FEATURES
PiSmart is an intelligent platform based on Raspberry Pi designed by SunFounder, integrating Speech to Text (STT), Text to Speech (TTS), and servo and motor control. It includes a 5-channel, 10-bit ADC, and utilizes the 8-channel digital built into the Raspberry Pi to make DIY programming easier, and enabling intelligent human interaction. PiSmart has been built into this fun smart robot kit, allowing you to build a car, program it to follow a line, avoid obstacles, and respond to your voice.
- Includes Raspberry Pi
- Based on the PiSmart platform
- PiSmart integrates speech recognition of STT, TTS, & servo and motor control
- Works for line following & obstacle avoidance w/ the ultrasonic & line follower modules
- Many pin headers allow you to install more sensors for function extension
- Supports graphical programming w/ Scratch for easy debugging
- Raspberry Pi 3
- M3x8 screw
- M3x10 screw
- M3x12 screw
- M2.5×12 screw
- M3x24 screw
- M3 nut
- Universal wheel
- Driven wheel
- Gear reducer
- 2S Li-Po battery
- PiSmart top PCB
- PiSmart bottom PCB
- Ultrasonic obstacle avoidance module
- Line follower module
- M2.5×10 bi-pass copper standoff
- M2.5×11+6 copper standoff
- M3x40+6 copper standoff
- 150mm HX2.54 3-pin jumper wire
- 150mm HX2.54 4-pin jumper wire
- 150mm DC5.5-2.1 specialized power cord
- 40mm FFC 0.5 40-pin reverse connecting line
- USB charger for Li-Po battery
- 3M velcro tape
PRODUCT SPECS
Includes

Air Selfie Drone + Power Bank Storage Case for $299





KEY FEATURES
AirSelfie is a revolutionary pocket-sized flying camera that connects with your smartphone to let you take HD aerial photos of yourself, your friends, and your life. Its turbo fan propellers can thrust to just over ten meters in the air letting you capture wide, truly original photos and videos on your device. With an anti-vibration shock absorber, 5 MP camera, and video streaming capabilities of 1080p @ 30fps, you can rest assured you’ll be getting only the highest quality images and video.
Successfully funded on Kickstarter
‘This is a fun, easy drone to use that takes nice quality video and images.’ Forbes
- Easily controlled right from your smartphone
- Features self-generated 2.4GHz WiFi network for constant communication w/ your device
- Safe to grab while hovering
- Slips easily into a custom fitting phone cover & charger making it supremely portable
- Portable power bank provides up to 20 charges
- Sophisticated sensors maintain stability for crisp imaging
- Boasts built-in 4GB micro SD memory card
PRODUCT SPECS
Details & Requirements
- Material: anodized aluminum
- Weight: 61 g
- Camera: 5 MP
- Video resolution: 1080p @ 30fps
- Built-in memory: 4GB
- WiFi: 2.4GHz
- Battery capacity: 240mAh
- Flight time: 3 minutes per charge
Compatibility
- iOS
- Android
Includes
- AirSelfie
- Power bank
- Collision protector
- USB cable
The Mindful Notebook for $21





KEY FEATURES
We beat Amazon’s price every time! See for yourself.
The Mindful Notebook is a tool to keep you focused and ensure you’re starting each day with the proper mindset to reach your goals and fulfill your objectives. The notebook has three parts which help you go about your day and tasks with ease. Start taking back control of your life today!
Successfully funded on Kickstarter
- Daily Inspirational quote included on each page to make sure you’re properly grounded
- Journal may be used an everyday go-to place for notes or thoughts
- Gratitude Patience section reminds you of what you can be grateful for
- Corso donates to the Foundation for a Mindful Society w/ every purchase
PRODUCT SPECS
Details & Requirements
- Dimensions: 8.5″ x 6.5″ x 5″
- Material: PU leather
Includes
- Mindful Notebook

Collage.com Custom Holiday Gifting: Store Credit for $24





KEY FEATURES
Collage.com provides the easiest and most versatile tools to help you turn your photos into priceless, enduring memories. Whether you’re designing a collage or printing a single image, creating the perfect custom product is fast, easy, and fun. From photo blankets to iPhone cases, Collage.com makes customizing your everyday life with a personal flair an absolute cinch.
As seen on Good Morning America, The View, DIY Network, Mashable, and Forbes
- Get $100 worth of credits to Collage.com
- Pick between over 50 custom products to customize
- Add your own photos & text to make any product your own
- $100 credit
- Items: photo blankets, mugs, photo books, calendars, canvases, framed prints, posters, metal prints, mounted prints, area rugs, beach towels, coasters, t-shirts, aprons, sweatshirts, pillows, blankets, iPhone/iPad cases, accessory bags, and more
- To browse the product library, click here
Note: Because Collage.com’s products are printed to order, don’t wait! View Valentine’s Day shipping deadlines at collage.com/deadlines. For most parts of the country, February 7 is the last date to order the most popular product, photo blankets, for arrival by Valentine’s Day with the fastest shipping method.
PRODUCT SPECS
Details & Requirements

Hera 2: World’s Most Advanced Dual-Use Vaporizer for $129





KEY FEATURES
Customers must be 21+ to purchase
Say hello to the most advanced and easy-to-use, dual-use vaporizer ever designed. With Hera2, you can seamlessly switch between Herbal & Extract modes for the ideal vaping experience. Unlike the leagues of other pocket vaporizers, this vaporizer is built to survive absolutely anything. It’s small enough to fit in your back pocket, but strong enough to produce thick, milky vapor in every session. Top-notch components, state-of-the-art technology and unyielding attention to detail show that their commitment to perfection is not just a statement. It is a promise so you can vape in peace, forever.
- Seamless switching between Dry Herb & Extract modes (dual-use)
- Ceramic & stainless steel hybrid dual-chamber
- Hybrid heating technology; high quality, dense vapor
- Compact sleek design; VUI touch screen
- High precision 100 different temperature settings ( 350°F-450°F)
- 2680 mAh Li-Ion replaceable battery; 90 minutes session time
- Active vibration, LED progress lighting control
Tobacco use only
PRODUCT SPECS
Details & Requirements
- 60-second heat up time
Includes
- Hera 2
- Dual chamber mouth piece
- Herbal concentrate mouth piece
- Carrying case
- Concentrate tool
- Cleaning brush
- User manual and warranty card

Cync Design Cuban Lynk MFi Lightning Cable Wristbands for $42





KEY FEATURES
This Cuban Lynk bracelet is inspired by the particular style of necklace called the Cuban Link. It draws a resemblance to a fancy piece of jewelry allowing you to remain fashion-forward, while tactfully hiding an incredibly useful accessory: a Lightning cable. Carry your charge and sync cable with you anywhere, without having to coil it up and stuff it in a purse.
- Cool Cuban link w/ gold bangle bracelet makes it a glamorous piece
- Offers a high-level of comfort for everyday wear
- MFi-Certified Lightning cable allows easy data transfer or charging
- Fits your wrist perfectly while still providing the ideal length for working w/ a portable power bank or external charger
- Firm welding materials makes the bracelet anti-sway & bend-resistant
PRODUCT SPECS
Details & Requirements
- MFi-Certified
- Fits wrists up to 6.75″ around
Includes
- Cync Design Cuban Lynk MFi Lightning Cable Single Loop Wristband
Pay What You Want: The Ultimate White Hat Hacker 2018 Bundle for $1
KEY FEATURES
Over this course you’ll learn network hacking techniques and vulnerability scanning to discover security risks across an entire network, learning skills for which companies are willing to pay top dollar. Whether you want to protect your own network or protect corporate networks professionally, this course will get you up to speed.
- Access 106 lectures & 12.5 hours of content 24/7
- Architect your network for maximum security & prevent local & remote attacks
- Understand the various types of firewalls available, including layer 4 firewalls like Iptables & PF
- Discuss firewalls on all platforms, including Windows, Mac OS, & Linux
- Explore wireless security & learn how WiFi is hacked
- Use tools like Wireshark, Tcpdump, & Syslog to monitor your network
- Dive into search engine privacy & tracking, learning how to mitigate tracking & privacy issues
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Nathan House has over 24 years experience in cyber security where he has advised some of largest companies in the world, assuring security on multi-million and multi-billion pound projects. He is CEO of Station X, a cyber security consultancy. More recently Nathan acted as the lead security consultant on a number of the UK’s mobile banking and payment solutions helping secure to date over £71Bn in transactions.
His clients have included; BP, ExxonMobil, Shell, Vodafone, VISA, T-mobile, GSK, COOP Banking Group, Royal Bank of Scotland, Natwest, Yorkshire bank, BG Group, BT, London 2012.
Over the years he has spoken at a number of security conferences, developed free security tools, and discovered serious security vulnerabilities in leading applications. Nathan’s qualifications and education include:
- BSc. (Hons) Computing ‘Networks & Communication’ 1st Class Honors
- SCF : SABSA Charted Architect Foundation
- CISSP : Certified Information Systems Security Professional
- CISA : Certified Information Systems Auditor
- CISM : Certified Information Security Manager
- ISO 27001 Certified ISMS Lead Auditor
- CEH : Certified Ethical Hacker
- OSCP : Offensive Security Certified Professional

KEY FEATURES
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. As you gain a complex understanding of websites, you will then learn how you can exploit them to carry out a number of powerful cyber attacks. You’ll track from a beginning to advanced level and by the time you finish you’ll be able to launch attacks and test the security of websites and apps the same way that black hat hackers would, and be able to fix these vulnerabilities.
- Access 93 lectures & 9 hours of content 24/7
- Learn how to gather information about your target site like discovering the DNS server used & subdomains
- Discover, exploit, & fix a number of vulnerabilities like file upload, code execution, SQL injection, XSS, & much more
- Understand what you can do w/ the access gained from vulnerabilities
- Explore the basic exploitation of attacks & the advanced methods to enhance them
- Learn how & why vulnerabilities are exploitable, how to fix them, & the right practices to avoid them
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Zaid Al-Quraishi is an ethical hacker, pentester, and programmer. He has extensive experience in ethical hacking and penetration testing, more specifically with regard to network security. Zaid started making video tutorials in 2009 for the ethical hacking website iSecuri1ty, and has also served as an editor, manager, and penetration tester for the company. He teaches mostly by example, specifically by first explaining the theory of each technique and then how it translates to a real-life situation.

KEY FEATURES
To break into the world of professional penetration testing, you’ll need to be an ace with Kali Linux. This course will introduce you to the latest ethical hacking tools and techniques with Kali Linux, using a testing lab for practicing different types of attacks. Across the course, you’ll simulate an entire penetration test from beginning to end, giving you verifiable hands-on experience.
- Access 80 lectures & 8.5 hours of content 24/7
- Get comfortable w/ Kali Linux & learn the penetration testing phases
- Manage Kali Linux HTTP & SSH services
- Discover essential tools like Netcat & WireShark
- Gather passive & active information
- Explore how to perform & defend against a variety of attacks
- Receive monthly virtual machines as a hacking challenge
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Mohamed Atef is an ICT Consultant, Senior Penetration tester and certified instructor with more than 20 years of experience in professional and academic courses and 2 books published.
- Certified Information System Security Professional (CISSP) ID #517943
- Microsoft Certified Trainer (MCT) ID #3022752
- EC Council Certified Instructor (CEI) ID #ECC51750391761
- CEH: Certified Ethical Hacking ID #ECC64515022319
- Certified Cisco System Instructor (CCSI)
- Microsoft Certified System Engineer (MCSE)
- Microsoft Certified IT Professional (Windows Server Administration 2008)
- CompTIA Certified (Network +) ID #
- CompTIA Certified (Server +)
- CompTIA Certified (Linux +)
- CompTIA Certified (Security +)
- Cisco Certified Network Associate (CCNA)ID #CSCO11273248
- Cisco Certified Network Professional (CCNP)
- Project Management Professional (PMP) )ID #1772374
KEY FEATURES
In this beginner- and professional-friendly course, you’ll learn how black hat hackers hack Windows using advanced techniques, while improving your knowledge on how to analyze and secure Windows, and detect a hacker’s identity. Across the example-based course, you’ll get hands-on instruction in white hat hacking.
- Access 81 lectures & 9 hours of content 24/7
- Learn how to download & setup Kali Linux 2.0, Windows 10, & Metasploit as virtual machines
- Understand how to gather as much info as possible from your target
- Use msfconsole interface like a professional
- Encode & combine the payload
- Gain full access over a target OS & learn how to interact w/ it using Meterpreter command line
- Perform various attacks over WAN network
- Detect & protect from all of the attacks discussed
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Saad Sarraj has been an Ethical Hacker since 2012. He founded the website iSecurityPro and has been educating people in Linux and Windows security tips through his YouTube channel over that time. He is always focused on the practical side in his teaching, and the theory behind every attack.

KEY FEATURES
This course provides a good starting point from which to learn ethical hacking and identify threats and vulnerabilities to secure your IT environment. You’ll begin with an introduction to the best tools around before diving into basic hacking technique, and ultimately going into real-life scenarios to get a hang of how hackers think.
- Access 14 lectures & 2 hours of content 24/7
- Discuss a basic introduction to reconnaissance
- Get hands-on experience working w/ Metasploit & testing the effectiveness of different defenses
- Learn about sniffing & how effective Man-in-the-Middle attacks can be
- Go through a coffee shop scenario to further your understanding
- Understand how hackers use networks to gain access to different systems
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Gary Dewey is an IT consultant specializing in security. A graduate of SUNY Broome’s computer security and forensics degree program in New York, he has attended numerous B-Sides conferences and spoken at B-Sides in Rochester, New York. Gary participated in the 2015 US Cyber Challenge held at Virginia Tech. He is an active member of the Triple Cities Makerspace, a non-profit organization dedicated to community collaboration and learning. He enjoys hiking and cats.
KEY FEATURES
To completely understand computer security, it’s vital to think outside the box. It’s not just about firewalls, Intrusion Prevention Systems, or antivirus. It’s also about tricking people into doing whatever a hacker wishes. A secure system, therefore, is also about informed people. This training is based on a practical approach of day-by-day situations contained labs based on real environments. The aim is to help you learn ethical hacking techniques and methodology used in penetration systems to better protect yourself and those around you.
- Access 85 lectures & 12.5 hours of content 24/7
- Cover both theoretical & practical aspects of ethical hacking
- Work in hands-on labs about hacking systems, networks, wireless, mobile, & websites
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Gabriel Avramescu is a Senior Information Security Consultant and IT Trainer. He works on an Internet security team focused on ethical hacking – deliberately and purposefully challenging the IT security assumptions, strategies, and methods of protecting vital assets and information by emulating an adversary.
KEY FEATURES
WAPTP v3.1 is a highly practical and hands-on training for web application penetration testing that covers the OWASP top 10 vulnerabilities. Starting with various terminologies of web technologies, you’ll build towards mapping an application for insecurities, and understanding how to identify and mitigate threats.
- Access 64 lectures & 8 hours of content 24/7
- Map an app for insecurities using various tools & tricks, including Burp Suite
- Explore serious vulnerabilities like SQL injection, cross-site scripting, cross-site request forgery, XXE attacks, & more
- Find & hunt each vulnerability through the points developers use to secure the web app at the time of development
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Atul Tiwari has more than 7 years of working experience in the information security field. He has trained more than 3,000 students in information security and penetration testing. With his expertise in web application penetration testing, Atul has performed penetration tests, security audits, and security analysis for private enterprise, governments, and security agencies to assist with cyber threats.
KEY FEATURES
This course aims to teach you in-depth WiFi hacking and security. Upon completion, you’ll be confident in breaking all types of WiFi encryption methods. Starting as a complete beginner with little to no knowledge of WiFi security and Kali Linux, you’ll learn the most important elements of WiFi hacking so you can begin applying them to a career in ethical hacking.
- Access 118 lectures & 7 hours of content 24/7
- Get an introduction to Kali Linux & network basics
- Learn how to passively & actively gather information
- Identify vulnerabilities in a target
- Overrun buffer memory, perform password attacks, attack WiFi networks, & more
- Discuss client side & server side web vulnerabilities
- Test & exercise your defenses to ensure they’re up to task by simulating real-world attacks
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
LearnPentest is a group of penetration testers and ethical hackers with an extensive background in web application security, web and software development, network administration and exploit development. They have over 7 years of professional experience in the cyber security domain. Their instructors hold some of the most valuable certifications in the cyber security domain including: OSCP, LPT, C|EH, CISSP, OSCE.

4-Piece Classic Queen Sheet Sets for $31

KEY FEATURES
This 4-piece classic sheet set was designed with your comfort in mind. Made of the finest imported double-brushed microfiber yarns, this sheet set elevates the standard in softness and breathability. It’ll be hard to get out of bed in the morning!
- Double-brushed microfiber for outstanding comfort
- 16″ deep pocket-fitted sheets are perfect for oversized mattresses
- Superior weave for durability & a buttery-soft touch
- Hypoallergenic & antimicrobial for allergy sufferers
- Fade-resistant & wrinkle-free
PRODUCT SPECS
Details & Requirements
- Size: Queen
- Color: aqua
- Material: 90 GSM microfiber
- Care: machine wash cold, tumble dry low
Includes
- Flat sheet
- Fitted sheet
- 2 pillowcases

Metal Tunes Bluetooth Speaker for $25



KEY FEATURES
FRESHeTECH continues their mission to make music as conveniently portable as possible with the Metal Tunes Bluetooth Speaker. This sturdy, compact speaker was designed to be taken anywhere and to fill any environment with your favorite music or podcasts. Whether you want a speaker for your bedside or for your next camping trip, take a look at Metal Tunes.
- Delivers 5 watts of sound through a portable speaker
- Built-in microphone allows you to take calls without missing a beat
- Full onboard music controls let you adjust the volume or change tracks without your phone
- Supports 6 hours of playtime on a single charge
PRODUCT SPECS
Details & Requirements
- Speaker: 5 Watts
- Battery life: 6 hours
- Charging time: 90 minutes
Includes
- Metal Tunes Bluetooth Speaker (black)
Fader Stealth Drone for $69





KEY FEATURES
There are few things the FADER quadcopter can’t do! Ready to fly right out of the box, this drone is loaded with advanced features that make flying a breeze for beginners, and a ton of fun for experts. Super stealthy, lightweight, and ticked out with a six-axis gyro module and awesome HD camera, the FADER looks like a special ops device and flies like it was designed for elite pilots.
- Auto take-off & land, altitude hold, & ready to fly technology make it extremely easy for beginners to use
- HD camera records incredible 720p views in real-time
- 6-axis flight control system w/ adjustable gyro sensitivity & 3-level adjustable controller sensitivity offers advanced flight options
- LED lights allow for night flights
- Aerobatic “flip” capability adds a flair of fun to every flight
PRODUCT SPECS
Details & Requirements
- Gyro: 6-axis gyro
- Frequency: 2.4GHz
- Channels: 4
- Battery: 3.7V, 520 mAh
- Flight time: about 7 minutes
- Charging time: 45 minutes
- Controller battery: 4 AAA (not included)
- Camera: HD (720p), 1 MP, 120º wide angle view
- Remote-controlled distance: up to 50m
- Dimensions: 6.89″ x 6.89″ x 1.57″
Compatibility
- Free app compatible with iOS or Android
Includes
- FADER quadcopter
- Controller
- USB charging cable
- User guide
- 4 replacement rotor blades

Levimoon: The World’s First Levitating Moon Light for $199





KEY FEATURES
The moon is a fascinating celestial object, its waxing and waning phases the inspiration for tomes of poetic tribute. Each night we see it differently in the sky, and with the world’s first levitating moon light, Levimoon, you’ll see it differently in your home, as well. This remarkable light levitates over its base and changes its light with the simple touch of a button.
Successfully funded on Kickstarter and Indiegogo
- Total restoration of the moon
- Slim & elegant docking
- Easy levitating operation
- Changeable brightness & colors
- Levitation can work 24/7 & recharge wirelessly
- Perfect as a mood light or night light
PRODUCT SPECS
Details & Requirements
- Moon light diameter: 15cm
- Levitating dock dimensions: 12.2cm x 12.2cm x 3cm
- Moon light material: PLA
- Base finish: walnut wood
- Lighting color options: warm yellow and cold white
- LED voltage: 0.1 Watt ~ 1.5 Watt
- Working hours: 10-100 hours
- Battery capacity: 600mAh rechargeable lithium battery
Includes
- Moon light
- Dock
- AC adapter
- Dock protector



