Tag Archive: Super

The Super-Sized Ethical Hacking Bundle for $43

KEY FEATURES
Internet security has never been as important as it is today with more information than ever being handled digitally around the globe. In the first course of this four volume bundle, you’ll get an introduction to hacking and how to protect yourself and others. You’ll develop an understanding of the threat and vulnerability landscape through threat modeling and risk assessments, and build a foundation for which to expand your security knowledge.
- Access 117 lectures & 11 hours of content 24/7
- Explore the Darknet, malware, exploit kits, phishing, zero day vulnerabilities, & more
- Learn about global tracking & hacking infrastructures that nation states run
- Understand the foundations of operating system security & privacy functionality
- Get a crash course on encryption, how it can be bypassed, & what you can do to mitigate risks
- Discover defenses against phishing, SMShing, vishing, identity theft, & other cons
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Nathan House has over 24 years experience in cyber security where he has advised some of largest companies in the world, assuring security on multi-million and multi-billion pound projects. He is CEO of Station X, a cyber security consultancy. More recently Nathan acted as the lead security consultant on a number of the UK’s mobile banking and payment solutions helping secure to date over £71Bn in transactions.
His clients have included; BP, ExxonMobil, Shell, Vodafone, VISA, T-mobile, GSK, COOP Banking Group, Royal Bank of Scotland, Natwest, Yorkshire bank, BG Group, BT, London 2012.
Over the years he has spoken at a number of security conferences, developed free security tools, and discovered serious security vulnerabilities in leading applications. Nathan’s qualifications and education include:
- BSc. (Hons) Computing ‘Networks & Communication’ 1st Class Honors
- SCF : SABSA Charted Architect Foundation
- CISSP : Certified Information Systems Security Professional
- CISA : Certified Information Systems Auditor
- CISM : Certified Information Security Manager
- ISO 27001 Certified ISMS Lead Auditor
- CEH : Certified Ethical Hacker
- OSCP : Offensive Security Certified Professional

KEY FEATURES
Did you know you can make money identifying and fixing bugs on some of the biggest web apps on earth? Last year, Facebook paid $5 million to independent hackers while Google paid over $6 million as part of their bug bounty programs. And they’re far from alone. In this course, you’ll learn how to legally hack major companies like Facebook, Google, and PayPal and get paid to do it.
- Access 72 lectures & 5.5 hours of content 24/7
- Learn how to get paid for hacking & disclosing bugs to major companies
- Get familiar w/ Burp Suite, browser plugins, & Kali Linux
- Explore types of vulnerability such as SQL, XSS, CSRF injection, & more
- Discover the methodology for performing bug bounty
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Amit Huddar is an Internet Entrepreneur and Software Engineer. He runs his own software company “Softdust,” which develops products for new technologies like wearables and other gadgets. He opted for computer science engineering in 2013 at SSIT and started his software company in his first year of engineering.
His skills include: Android app development, HTML, CSS, PHP, C, C++, JAVA, Linux, Building Custom Linux OS, Cloud Computing. Penetration testing, Kali Linux and Hacking.

KEY FEATURES
This course is targeted towards aspiring information security professionals who aren’t sure where to start. Beginning with basic security fundamentals, this course elevates through more advanced topics, ultimately providing you with the knowledge you need to pass the globally-recognized CompTIA Security+ certification exam.
- Access 67 lectures & 10.5 hours of content 24/7
- Cover basic security fundamentals, threats, & vulnerabilities
- Explore network security
- Dive into host & application security
- Discuss risk management & business continuity planning
- Study to ace the CompTIA Security+ certification exam on the first attempt
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Mohamed Atef is an ICT Consultant, Senior Penetration tester and certified instructor with more than 20 years of experience in professional and academic courses and 2 books published.
- Certified Information System Security Professional (CISSP) ID #517943
- Microsoft Certified Trainer (MCT) ID #3022752
- EC Council Certified Instructor (CEI) ID #ECC51750391761
- CEH: Certified Ethical Hacking ID #ECC64515022319
- Certified Cisco System Instructor (CCSI)
- Microsoft Certified System Engineer (MCSE)
- Microsoft Certified IT Professional (Windows Server Administration 2008)
- CompTIA Certified (Network +) ID #
- CompTIA Certified (Server +)
- CompTIA Certified (Linux +)
- CompTIA Certified (Security +)
- Cisco Certified Network Associate (CCNA)ID #CSCO11273248
- Cisco Certified Network Professional (CCNP)
- Project Management Professional (PMP) )ID #1772374

KEY FEATURES
To break into the world of professional penetration testing, you’ll need to be an ace with Kali Linux. This course will introduce you to the latest ethical hacking tools and techniques with Kali Linux, using a testing lab for practicing different types of attacks. Across the course, you’ll simulate an entire penetration test from beginning to end, giving you verifiable hands-on experience.
- Access 80 lectures & 8.5 hours of content 24/7
- Get comfortable w/ Kali Linux & learn the penetration testing phases
- Manage Kali Linux HTTP & SSH services
- Discover essential tools like Netcat & WireShark
- Gather passive & active information
- Explore how to perform & defend against a variety of attacks
- Receive monthly virtual machines as a hacking challenge
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Mohamed Atef is an ICT Consultant, Senior Penetration tester and certified instructor with more than 20 years of experience in professional and academic courses and 2 books published.
- Certified Information System Security Professional (CISSP) ID #517943
- Microsoft Certified Trainer (MCT) ID #3022752
- EC Council Certified Instructor (CEI) ID #ECC51750391761
- CEH: Certified Ethical Hacking ID #ECC64515022319
- Certified Cisco System Instructor (CCSI)
- Microsoft Certified System Engineer (MCSE)
- Microsoft Certified IT Professional (Windows Server Administration 2008)
- CompTIA Certified (Network +) ID #
- CompTIA Certified (Server +)
- CompTIA Certified (Linux +)
- CompTIA Certified (Security +)
- Cisco Certified Network Associate (CCNA)ID #CSCO11273248
- Cisco Certified Network Professional (CCNP)
- Project Management Professional (PMP) )ID #1772374

KEY FEATURES
In this course you’ll start with the basics of social engineering and elevate to an advanced enough level to be able to hack into all major operating systems, generate different types of Trojans, and deliver them using smart social engineering practices. Focused on the practical side of penetration testing, you’ll first set up a lab before getting real practice with penetration testing that will help you build a career and protect yourself from malicious hacking.
- Access 105 lectures & 11.5 hours of content 24/7
- Learn how to gather information about your target
- Generate evil files like backdoors, keyloggers, credential harvesters, & more for Windows, macOS, & Linux
- Discover a number of social engineering methods to deliver Trojans to a target like creating fake websites
- Interact w/ the systems you’ve compromised by accessing the file system, escalating your privileges, & more
- Learn how to protect yourself & your systems from these attacks
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Zaid Al-Quraishi is an ethical hacker, pentester, and programmer. He has extensive experience in ethical hacking and penetration testing, more specifically with regard to network security. Zaid started making video tutorials in 2009 for the ethical hacking website iSecuri1ty, and has also served as an editor, manager, and penetration tester for the company. He teaches mostly by example, specifically by first explaining the theory of each technique and then how it translates to a real-life situation.

KEY FEATURES
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. As you gain a complex understanding of websites, you will then learn how you can exploit them to carry out a number of powerful cyber attacks. You’ll track from a beginning to advanced level and by the time you finish you’ll be able to launch attacks and test the security of websites and apps the same way that black hat hackers would, and be able to fix these vulnerabilities.
- Access 93 lectures & 9 hours of content 24/7
- Learn how to gather information about your target site like discovering the DNS server used & subdomains
- Discover, exploit, & fix a number of vulnerabilities like file upload, code execution, SQL injection, XSS, & much more
- Understand what you can do w/ the access gained from vulnerabilities
- Explore the basic exploitation of attacks & the advanced methods to enhance them
- Learn how & why vulnerabilities are exploitable, how to fix them, & the right practices to avoid them
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Zaid Al-Quraishi is an ethical hacker, pentester, and programmer. He has extensive experience in ethical hacking and penetration testing, more specifically with regard to network security. Zaid started making video tutorials in 2009 for the ethical hacking website iSecuri1ty, and has also served as an editor, manager, and penetration tester for the company. He teaches mostly by example, specifically by first explaining the theory of each technique and then how it translates to a real-life situation.

KEY FEATURES
This course allows you to follow, in real time, each stage of a penetration testing engagement so you cna tweak and train your skills over and over again. You’ll get the latest tools and techniques using Rapid 7’s tool Metasploit to exploit targets, as well as run post exploitation techniques and utilize PowerShell with Empire. By giving you interactive, hands-on experience, you’ll be able to learn more efficiently and build a lucrative career as a penetration tester.
- Access 23 lectures & 3 hours of content 24/7
- Understand how to move around Metasploit
- Learn how to not be seen by intrusion detection system & evade anti-virus software used by professional penetration testers
- Explore Empire, how to gain sessions known as “agents,” escalate privileges & migrate over to the Metasploit framework
- Discover penetration tactics in real-time through visual learning
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Nick Smith has substantial experience in Networking & Systems Management covering Windows, *nix & Mac. He has worked from the ground up as a Systems Administrator / Network Administrator, ISP, Provisioning Broadband services & MPLS Networks in large corporate environments. He has been involved in running penetration test engagements within the Financial Sector Services for some of the largest global banking Institutes. Nick currently holds the Qualys Vulnerability Assessor Certification, & will explore CREST and others when he has time in the future.

KEY FEATURES
This course will give you an in-depth look into WiFi hacking and security. By course’s end, regardless of experience, you’ll be confident breaking all types of WiFi encryption methods and be ready to start pursuing a career in network security.
- Access 21 lectures & 3 hours of content 24/7
- Learn how to properly prepare your working environment
- Explore some basics about networks & how they work
- Discover every possible attack you can perform on a target network without being connected to it
- Crack & bypass security mechanisms of a network
- Understand how to anonymously stay on the network without being noticed
- Reduce the risk of being hacked by learning to secure your network
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
LearnPentest is a group of penetration testers and ethical hackers with an extensive background in web application security, web and software development, network administration and exploit development. They have over 7 years of professional experience in the cyber security domain. Their instructors hold some of the most valuable certifications in the cyber security domain including: OSCP, LPT, C|EH, CISSP, OSCE.

KEY FEATURES
You hear about it all the time: companies getting hacked, having their websites shut down or their customers’ data compromised. When that happens, it’s time to call in ethical hackers to break into network systems, evaluate their security, and propose solutions. After this course you’ll be well on your way to being one of these hackers, paid generously to hack networks, apps, emails, social media accounts, and more!
- Access 89 lectures & 16 hours of content 24/7
- Understand how to bypass different security layers after getting proper approval
- Learn how to compromise computers, crack passwords, crash systems & compromise applications
- Run a buffer overflow from scratch
- Stride towards a career in this fast-growing IT profession
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Mohamed Atef is an ICT Consultant, Senior Penetration tester and certified instructor with more than 20 years of experience in professional and academic courses and 2 books published.
- Certified Information System Security Professional (CISSP) ID #517943
- Microsoft Certified Trainer (MCT) ID #3022752
- EC Council Certified Instructor (CEI) ID #ECC51750391761
- CEH: Certified Ethical Hacking ID #ECC64515022319
- Certified Cisco System Instructor (CCSI)
- Microsoft Certified System Engineer (MCSE)
- Microsoft Certified IT Professional (Windows Server Administration 2008)
- CompTIA Certified (Network +) ID #
- CompTIA Certified (Server +)
- CompTIA Certified (Linux +)
- CompTIA Certified (Security +)
- Cisco Certified Network Associate (CCNA)ID #CSCO11273248
- Cisco Certified Network Professional (CCNP)
- Project Management Professional (PMP) )ID #1772374

The Work-At-Home Super Bundle for $39


KEY FEATURES
Working as your own boss is an exciting and fulfilling way to make it in the world, but it’s not without its own challenges. From marketing your business online to ideal legal and accounting practices, this colossal collection is loaded with ebooks, online courses, and more to help you navigate through them all and kickstart your self-employed venture with your best foot forward.
- Access 23 eBooks, 1 audiobook, 9 online courses & 4 printable packs 24/7
- Learn how to source & identify better work-from-home opportunities
- Market your business online w/ simple social media strategies
- Create clear work & home life boundaries to stay balanced
- Use tips & templates to get started as a freelance writer or editor
- Discover financial & legal tips to grow your business
For the full list of content, click here
PRODUCT SPECS
Details and Requirements
- Length of time users can access this course: lifetime
- Access options: web
- Certification of completion included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required

The Pay What You Want 2018 Super Mac Bundle for $1



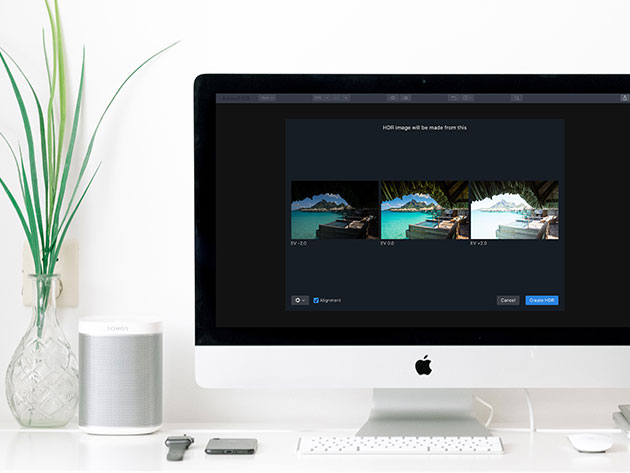

The Pitch
Aurora HDR Express is the streamlined version of the world’s leading HDR photo editor. Take advantage of this high-powered software, and turn your ordinary photos into stunning HDR photos in no time. Created as a joint project between Skylum and Trey Ratcliff, the world’s foremost HDR photographer, this photo software brings together everything other HDR editors are missing, and more.
- Load your TIFF, JPEG, or PNG & watch Aurora HDR Express do its magic
- Create amazing HDR photography from single photos or multiple brackets
- Access an enormous range of editing functions & tools
- Share your photography directly to social media
System Requirements
- MacBook, MacBook Air, MacBook Pro, iMac, iMac Pro, Mac Pro, Mac mini
- Mac OS X 10.10.5 or later
- Processor: Intel 64-bit Core 2 Duo or better
- 4 GB RAM or more
- 2GB hard disk space, SSD for best performance
- Display resolution 1280 x 768 or higher
Important Details
- Redemption: must redeem within 30 days of purchase
- Restrictions: for use on up to 5 devices
- Version 1.2.2
- Image formats: PNG, JPG, TFF 8-bit and 16-bit, GIF, PSD, and more
About the Developer
Skylum is a team of professional photographers and software building experts. We love capturing moments. And we want to help others to create the most incredible images in less time. We have a goal to bring photographers around the world a first worthy Adobe alternative. And we know we can make it happen. That’s why we put our hearts and souls into Aurora HDR and Luminar. Millions of people on Mac and PC already use our software to effortlessly make beautiful images, and so can you. Let’s change the photography world for better.
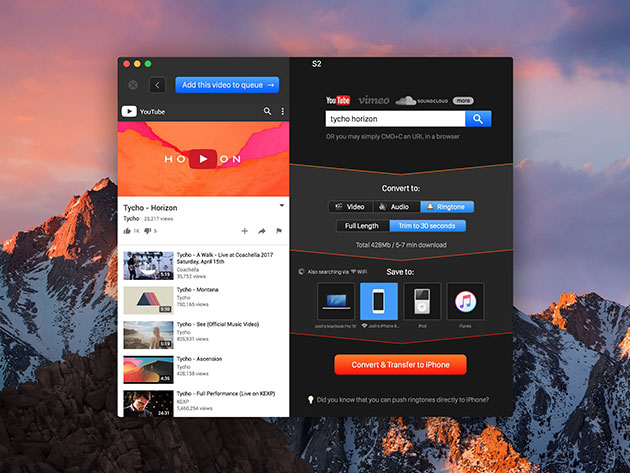
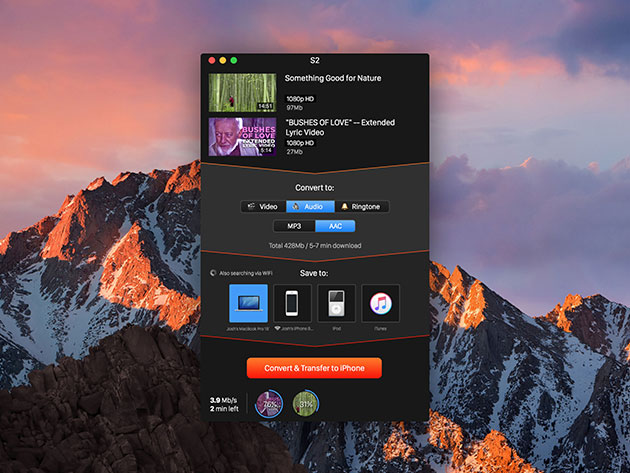
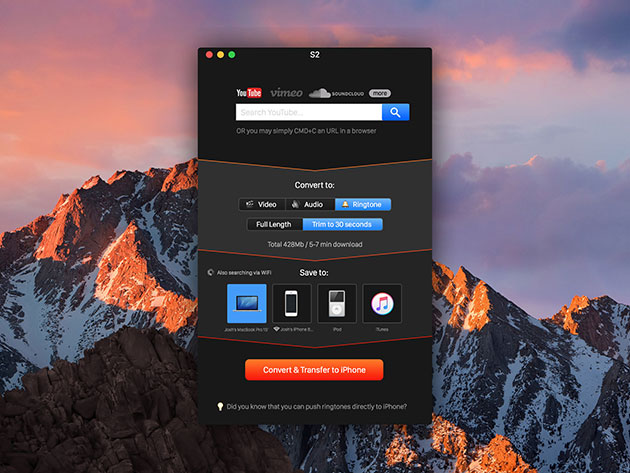
The Pitch
YouTube is a massive video and music library, but its only significant flaw is that you need internet access to use it. Well, not anymore. Softorino YouTube Converter 2 lets you quickly download any YouTube video to your Mac’s desktop or other Apple devices, so you can watch it offline and without the stop-and-go loading that comes with spotty streaming. Unlike other Youtube converters, Softorino goes beyond videos and music, as it can even turn any YouTube video into a trimless iPhone ringtone.
- Download & watch videos w/ 4K, 1080p FullHD and 60fps support
- Turn any online video into an MP3 song
- Enjoy full subtitles support
- Transfer videos to your iPhone & iPad w/ 1 click
- Download videos to create your own ringtones
System Requirements
- MacOS 10.10 and later
- Windows 10 and later
- iOS 5 and later
- All iPod devices
Important Details
- Redemption: must redeem within 30 days of purchase
- Updates included
- Restrictions: 1 user per license
- Supports 4K, 1080p FullHD and 60fps
About the Developer
We’re Softorino – a purely European crew packed with talented developers, designers & managers. Since the fall of 2011, we apply all of our focus into bringing simple solutions & fresh design into the world of Mac OS X & Windows.

The Pitch
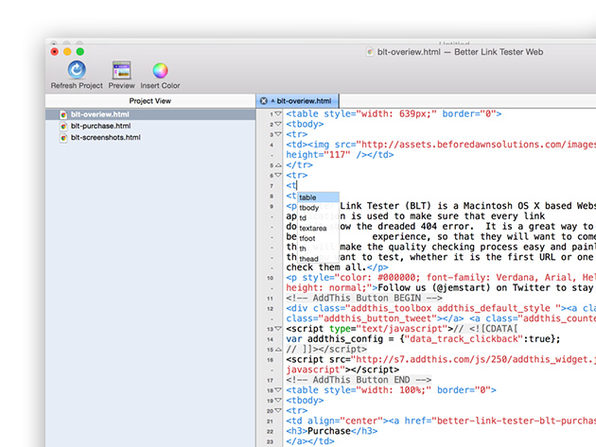
Want to design and develop websites faster and more efficiently? skEdit is the feature-rich app that stays out of your way while you build. Highly customizable, with a powerful snippet and code system, skEdit lets you work fast, automate repetitive tasks, make project-wide updates fast, and much more.
- Support for Subversion source control management is built in
- Integrated HTML Tidy support lets you clean up your markup
- Code completion for built-in functions, classes, etc let you work more quickly
- Extensible editing lets you easily add support for new languages or tweak existing languages
- Preview as plain HTML or run the file through your web server first
- Edit files over FTP, SFTP, or WebDAV using the same interface used for any files
- User scripts let you write in the language of your choice to automate common tasks
- Easily perform project-wide search & replace
Reviews
- CNET: ★★★★★
System Requirements
- Mac OS X 10.8 or later
Important Details
- Redemption: must redeem within 30 days of purchase
- Version 4.1.17
- Minor updates included
- Currently supported languages: Action Script, ASP, Cold Fusion, CSS, HTML, JavaScript, MovableType, Perl, PHP, Python, Ruby, Ruby on Rails, SQL
About the Developer
Before Dawn Solutions is small startup based in Denver Colorado, that focuses on doing technology stuff. Whether it is Application development (Mac/iOS/Web) or putting together customized hosting solutions for our customers. We love doing it and it shows in our work.

The Pitch
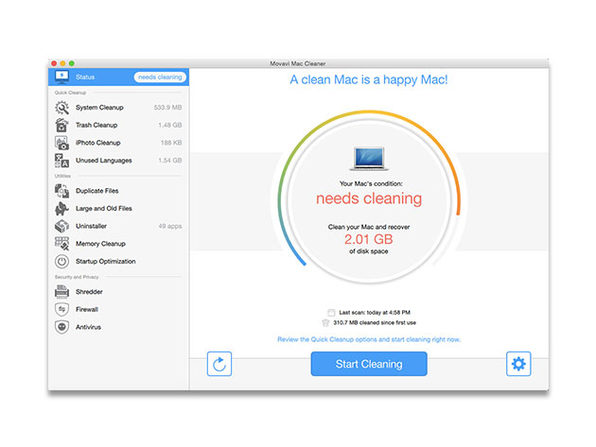
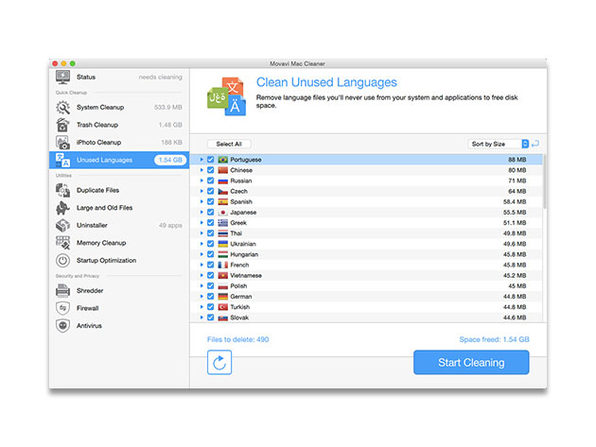
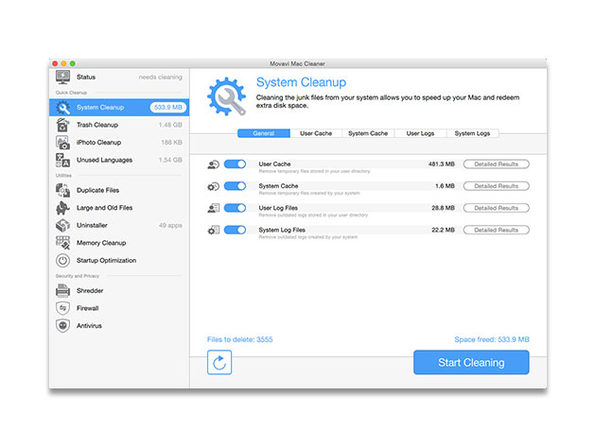
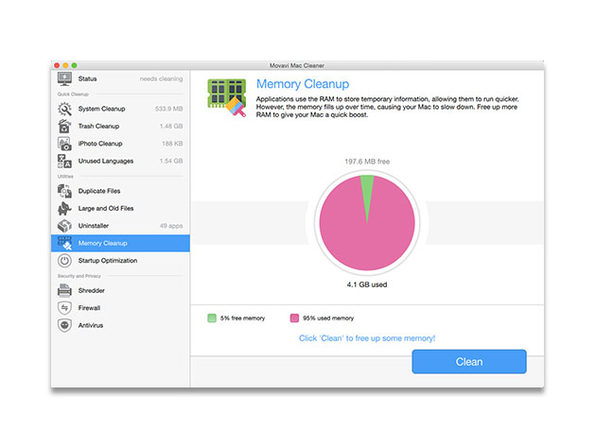
Ever seen that “startup disk is almost full” window pop up, and then go about cleaning out your big files? That’s a very, very limited solution. Run Movavi Mac Cleaner and you’ll be amazed how many unnecessary cache files, logs, app localizations, and image files have been clogging up your Mac. This software is smart enough to identify the files that can safely be deleted, plus it will protect your computer from viruses and network attacks. Want to keep that startup disk window at bay? Clean your Mac with Movavi Mac Cleaner.
- Remove unnecessary log files & empty all trash bins
- Clear user & system caches
- Delete unused app localizations
- Completely uninstall apps together w/ their support files
- Secure your computer from internet threats
- Improve the speed & stability of your Mac
- Turn on automatic cleanups so your system is always in the best shape
System Requirements
- Mac OS X 10.7 or alter
- 64-bit Intel processor
- 1024 x 768 screen resolution, 32-bit color
- 512 MB RAM
- 100 MB hard disk space for installation, 1 GB for ongoing operations
Important Details
- Redemption: must redeem within 30 days of purchase
- Version 2.4.2
- Updates included
About the Developer
Movavi produces a wide range of multimedia programs that ensure you can have fun with your videos, music, and photos on any platform and any device. We develop easy-to-use, powerful and effective programs that inspire people to process, enhance, and share their content. Our key expertise is seamless video conversion across all popular multimedia formats.
In addition to over 20 standalone applications, Movavi produces a complete multimedia suite, which includes tools for video conversion, PC screen capturing, video editing and playback, online sharing and disc burning.
Since its establishment in 2004, Movavi has grown from a small startup run by three enthusiasts who produced and supported two products to an international business with over 100 employees and an expanding product range for PC and Mac sold in 150 countries. The company’s US office is located in Saint Louis, Missouri, USA.

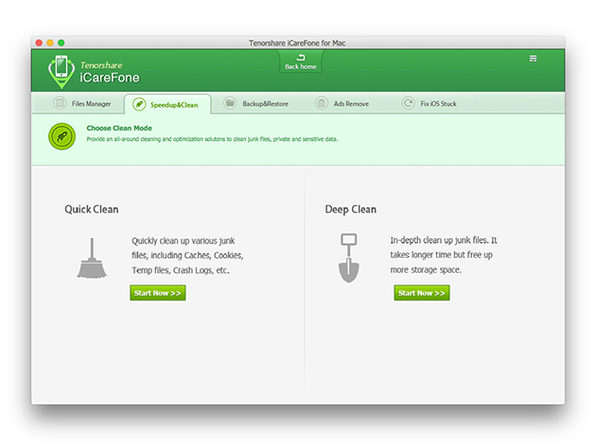
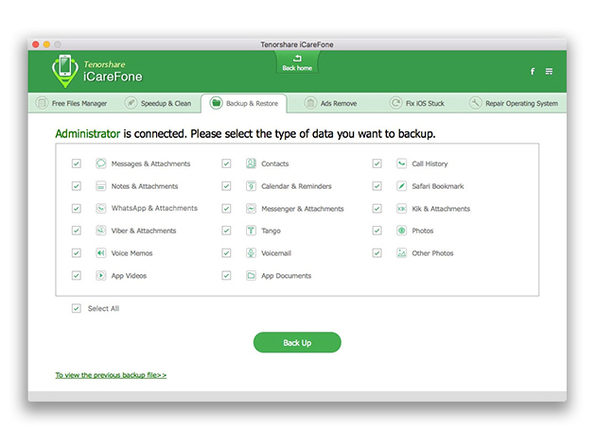
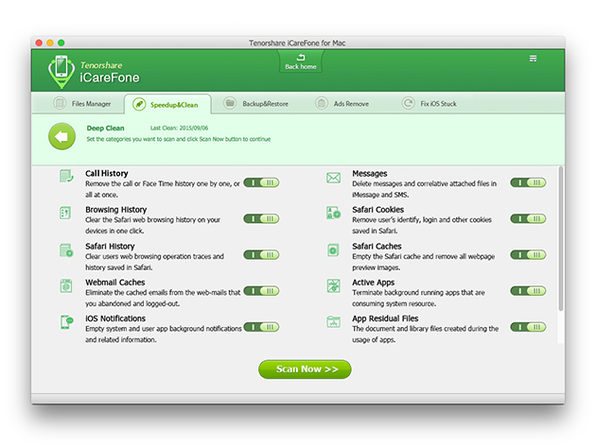
The Pitch
It’s only natural that your iPhone starts to lag after some time, right? Maybe. But it also could just mean that you’re not properly caring for your device that way you care for your laptop. Tenorshare iCareFone for Mac takes a one-click approach to protecting, repairing, cleaning, optimizing, and eventually speeding up your iPhone, iPad and iPod. Solve all your iOS issues with ease and finally get the performance you have come to expect from an Apple product. Plus, with this purchase, you’ll enjoy a lifetime of major and minor updates.
- Transfer photos & music between iPhone and Mac w/ one click
- Easily organize & manage contacts, photos, apps & music
- Organize & manage 8 types of files: Contacts, Notes, Calendars, Apps, Music, Videos, Bookmarks & Photos
- Export & transfer files to your computer in the form of xls, .doc, .txt, .pdf, .jpg & more
- Easily add or delete files from your iPhone
- Merge duplicated contacts on your iPhone/iPad/ iPod
Reviews
- CNET Editors: ★★★★★
- TopTenReviews: ★★★★★
System Requirements
- Mac OS X 10.6 or later
Important Details
- Redemption: must redeem within 30 days of purchase
- Length of access: lifetime
- Restrictions: for activation on 1 computer
- Version 3.3
- Major upgrades and minor updates included
What’s the Difference Between a Standard & Lifetime License?
Great question! A Standard License issues full access to the app and all minor updates for life. Minor updates usually include fixes to bugs that surface post-launch. As you know, when an app gets a major update (and advances to the next version e.g. V2, V3, V4), older versions often grow obsolete. Perhaps it no longer works properly with your new computer or OS, or maybe you’re simply missing out on serious improvements and experiencing some major FOMO.
That’s why a Lifetime License is so appealing. You’ll get a lifetime of major updates, and inevitably a world of new features that are beyond our current imagination. Many of our Lifetime License options are exclusive offers, at the web’s best prices.
About the Developer
Tenorshare is an international IT software company that is established in 2007. We have created quite a lot of highly-rated branded software products that won many official awards. Tenorshare aims to employ the most talented employees to develop the highest-level products. Better software, better life!





The Pitch
Whether you need to transfer a few files or a few thousand, schedule automatic backups, or perform website maintenance, Yummy FTP Pro will handle it with ease. This easy-to-use Mac file transfer app provides a full-featured professional toolkit that’s blazing fast and reliable. If you need to move some files around, Yummy is your solution.
- Access full FTP/S, SFTP & WebDAV/S protocol support
- Simplify site management w/ file organization, editing, diff, preview & sync tools
- Schedule one off or repeating transfer or folder synchronization tasks
- Create FTP drop folders on your Desktop for quick & easy uploading
- Get started faster w/ the intuitive user interface
- Enjoy frequent, free maintenance & updates
Reviews
-
MacUpdate: ★ ★ ★ ★ ★★
System Requirements
- MacOS X 10.8 and later
Important Details
- Redemption: must redeem within 30 days of purchase
- Restrictions: 1 license covers personal use on all of your Macs
- Updates included
About the Developer
Yummy Software is a small UK-based independent software company, dedicated to creating the very best Mac FTP software. The company is owned and run by Mac enthusiasts and the developers have worked on various commercial products spanning over three decades, right back to the original Apple Macintosh. Our dedication to the Mac platform runs deep, and our appreciation for good software is what drives us to release the best Mac FTP apps around.





The Pitch
Accidents happen, which is why it’s critical to have a data recovery system at your disposal. Disk Drill Pro makes it easy to recover documents, music, photos, videos, or even whole partitions that have gone missing from your computer. With just a single push of a button, Disk Drill can recover over 200 types of files on your computer or even on external drives when you connect to a computer. Don’t get caught in a pinch by losing data – Disk Drill Pro is your insurance policy.
- Use just one recover button to get all your needs covered
- Scan & recover data from virtually any storage device w/ just the click of a button
- Recover any file or folder or reconstruct over 200 file types w/ multiple recovery methods
- Connect your mobile or storage device & recover data from it in minutes
Reviews
- Macworld: ★★★★★
System Requirements
- Mac OS X 10.8.5 or later
Important Details
- Redemption: must redeem within 30 days of purchase
- Restrictions: available for 1 user and 3 computers
- Length of access: lifetime
- Version 3.5.890
- Minor updates included
What’s New in Version 3.5.890
- Quick Scan for APFS
- Support for data recovery on encrypted APFS partitions
- Support for external APFS drives on macOS 10.13.x
- Scanning results got new folder names that correspond to the actual recovery algorithms
- Recovery session management for APFS drives
- Some random fixes in multiple Disk Drill modules
About the Developer
Do you need to recover deleted files in Mac OS X, such as critical business documents, music, photos or videos? Have files or whole partitions gone missing from your Mac? Are you having trouble accessing an external USB drive or camera card? We can help. We make data recovery for Mac OS X easy.

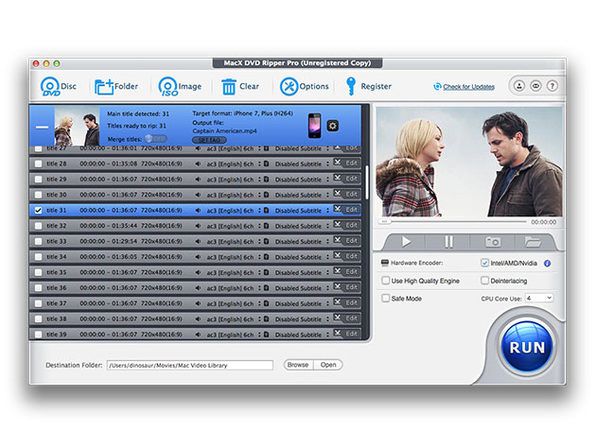
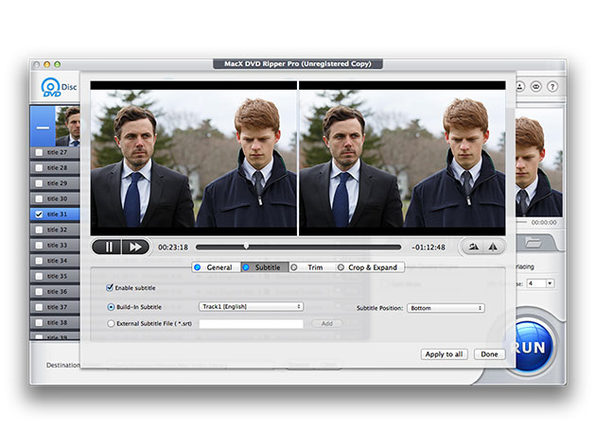
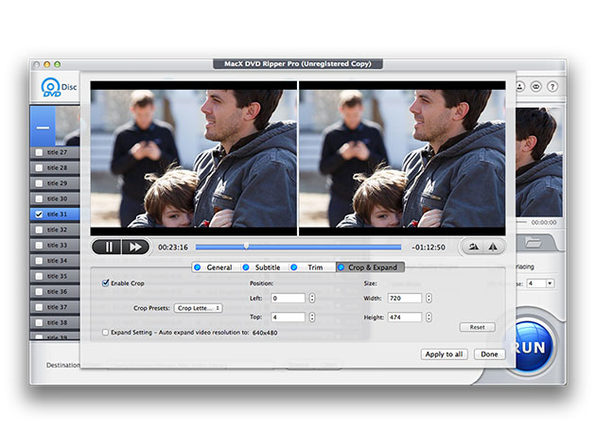
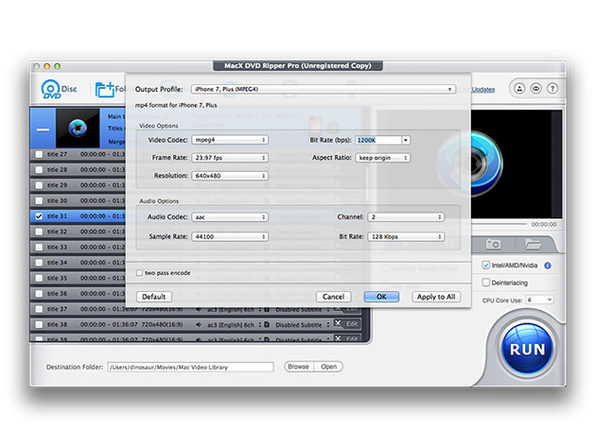
The Pitch
Watch your favorite DVD on your iPad (or other mobile device) without buying an additional digital copy thanks to this convenient software. MacX DVD Ripper is the fastest DVD ripper for Mac and even supports batch converting for multiple videos at once.
- Convert DVDs to popular video/audio formats for convenient viewing
- Decrypt copy-protected DVDs
- Trim, crop, merge, add external subtitles, cut video clips/segments, crop frame size, combine separate movies titles into a single video file & add subtitles
- Upload DVD videos or segments to YouTube
- Adjust parameter settings
- Extract audio & snapshot images from DVD
System Requirements
- Mac OS X 10.5 or later
Important Details
- Redemption: must redeem within 30 days of purchase
- Version 5.5.0
- Minor updates included
- Languages: English, Japanese, Traditional Chinese, Simplified Chinese, German, Italian, French, Portuguese, Spanish, and Korean
- Compatible inputs: the latest encrypted DVD, CSS protected DVD, region 1-6, Sony ArccOS, commercial DVD, ISO image, DVD media, normal DVD
- Compatible outputs: DVD ISO image, MPEG-2 (DVD), MKV, MP4, QT, MOV, M4V, FLV, H.264, MPEG4, AVI XviD/DivX, MTS, TS, M2TS, iTunes, iPod (iPod classic, iPod touch, iPod nano), iPhone (iPhone 6s/6s Plus, iPhone 6/6 Plus, iPhone 5S/5C/5, iPhone 4S/4 and more), iPad, Apple TV 3, PSP, MP3, PNG, etc
About the Developer
Digiarty Software, a leading multimedia software provider, focuses on DVD/Video converting and backup, iPhone iPad transfer and management solutions. Since it’s foundation in 2006, Digiarty has delivered easy-to-use and innovative applications to more than 8,000,000 users all over the world.
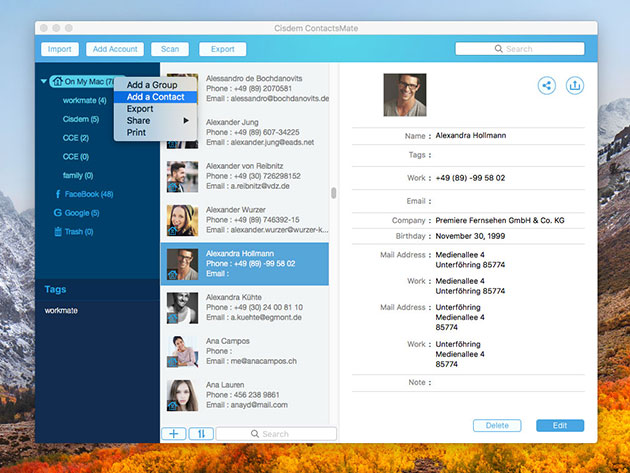
The Pitch
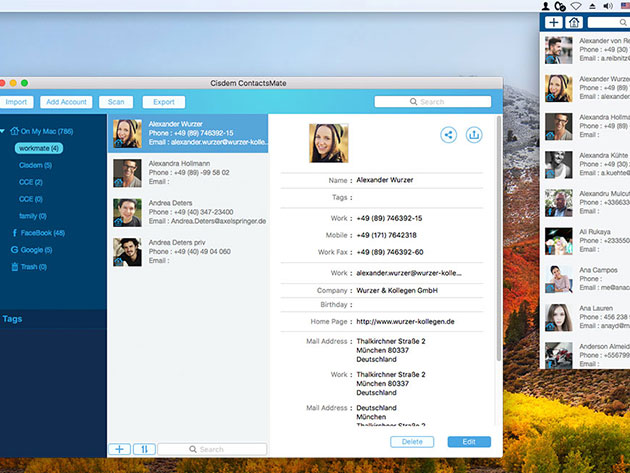
You acquire contacts through so many different platforms and mediums it can be difficult to ensure you have everyone in the right place. ContactsMate 4 is the solution. This best-selling contact manager enables you to easily import contact lists directly from a CSV or vCard file and syncs with your built-in contacts app and a wide range of cloud services to refresh your contacts list in minutes. But it doesn’t stop there. ContactsMate also allows you to connect easily through group messages or emails and lets you add and edit custom fields to make your contact list as up to date and easily searchable as possible.
- Import contacts from CSV & vCard, and sync contacts from Google, iCloud, Exchange, Facebook, Twitter, LinkedIn, and more
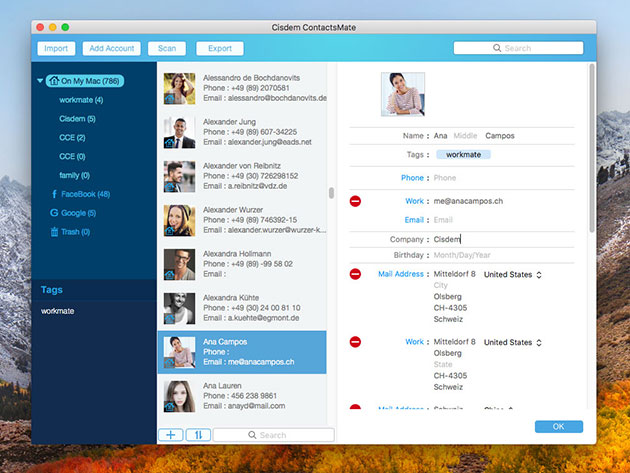
- Easily view, add, edit, group, tag, & manage contacts
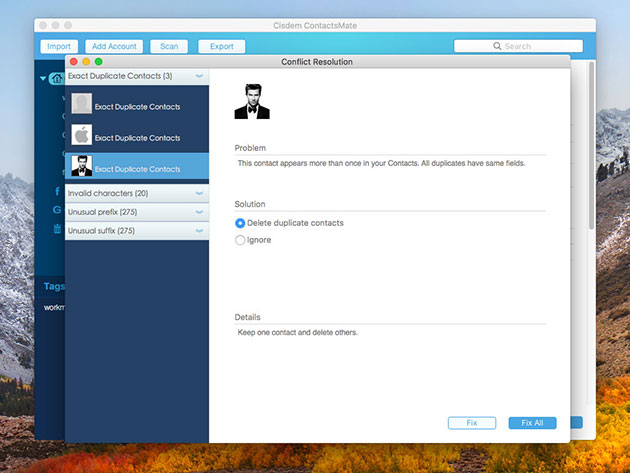
- Delete duplicate contacts & fix formatting errors
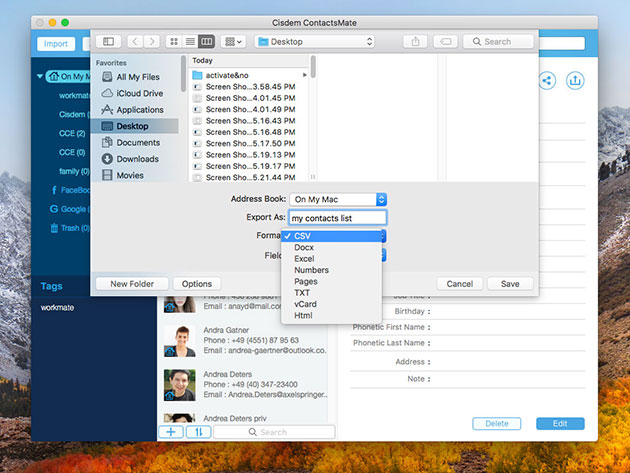
- Share, export & back up contacts to quickly exchange information
- Manage contacts by groups based on sources, interests, affinities & more
- Apply tags to sub-categorize contacts
- Find what you want w/ the intelligent multi-conditional search feature
- Send group messages, emails or start a call to your assigned contacts
Reviews
- Softpedia: ★★★★★
- Mac.informer: ★★★★★
System Requirements
- Mac OS X 10.11 or later
Important Details
- Redemption: must redeem within 30 days of purchase
- Length of access: lifetime access to all future minor updates and major upgrades
- Restrictions: for use on 1 computer
- Version 4.2
What’s the Difference Between a Standard & Lifetime License?
Great question! A Standard License issues full access to the app and all minor updates for life. Minor updates usually include fixes to bugs that surface post-launch. As you know, when an app gets a major update (and advances to the next version e.g. V2, V3, V4), older versions often grow obsolete. Perhaps it no longer works properly with your new computer or OS, or maybe you’re simply missing out on serious improvements and experiencing some major FOMO.
That’s why a Lifetime License is so appealing. You’ll get a lifetime of major updates, and inevitably a world of new features that are beyond our current imagination. Many of our Lifetime License options are exclusive offers, at the web’s best prices.
About the Developer
We are Cisdem, a dynamic group of people that are passionate about what we do. Our mission is to develop Mac software that is innovative, easy-to-use and budget friendly.
At Cisdem, we create innovative and high-efficient software in the fields of PDF Tools, Utility Tools, Mobile Tools, and Multimedia Tools. Cisdem Apps, known for their simple and user-oriented design, have been used by individual and business users in more than 100 countries. We do hope that our apps saved your time, money and efforts – be it recovering your lost data, signing an agreement, converting and editing PDF files, DVD burning, downloading videos, managing Mac Contacts, removing duplicate files, or cleaning junk files for mobile device. Ultimately, our goal continues to be, providing flexible, cost effective tools that make life easier and processes simpler.

The Pitch
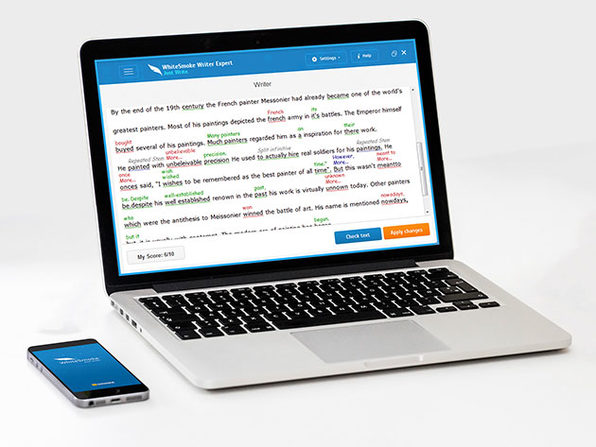
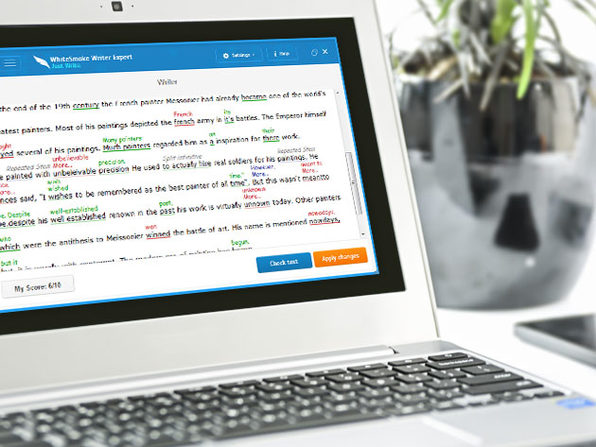
Even the best writers make errors. Whether you fit that mold or you’re an awful writer altogether, you’ll find your solution in WhiteSmoke. Using advanced technology, WhiteSmoke checks your work for grammar, spelling, punctuation, and style errors – so you never send off a flawed work email again. Whether you’re writing on mobile or desktop, this versatile, easy-to-use software is compatible with all browsers, includes a translator for over 50 languages, and lets you perfect your writing virtually anywhere you do it.
- Rated as the #1 solution for English grammar, style, spelling & punctuation
- Activates w/ just one click in browser-based text editors
- Analyzes text w/ unique patented artificial intelligence algorithms
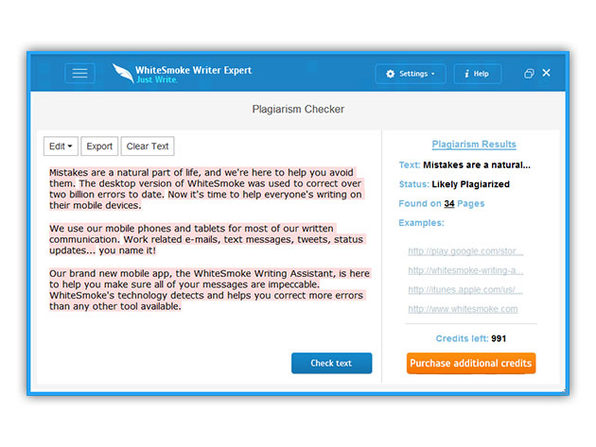
- Checks for potential plagiarism w/ its huge database
- Works w/ Microsoft Word & Outlook to proofread your emails and documents
Reviews
- TopTenReviews: 2017 Gold and Excellence Award for Writing Enhancement Software
System Requirements
- macOS Sierra
- All web browsers
Important Details
- License redemption deadline: redeem within 30 days of purchase
- Restrictions: includes license for 1 user
- Length of access: 2 years
- Updates included for 1 year
- Premium includes Anywhere & Writer Expert
- Includes spelling, grammar, punctuation, style & plagiarism checker
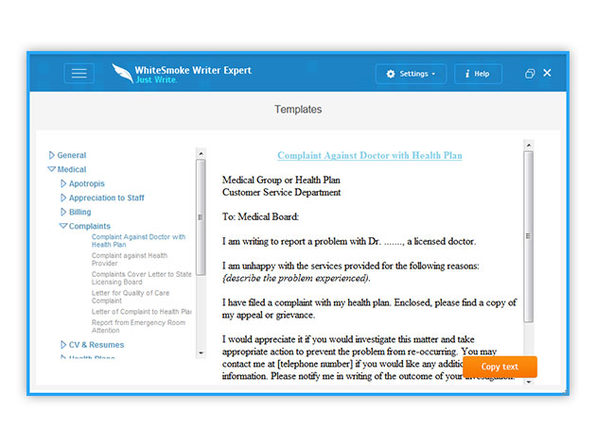
- Includes writing tutorials, document & letter templates
- Full text translator & dictionary for over 50 languages
- English grammar video tutorials
About the Developer
We produce an all-in-one English writing tool that provides grammar, spelling, punctuation and style checks. Our software is activated in a single click from any text application and browser, pointing out potential errors for consideration and offering suggestions for improvement. We believe that users that have little or no experience with WhiteSmoke software can use our solution to quickly begin writing, editing, translating and enhancing their English documents.
Our software serves a large and growing market of both native and non-native English speakers and provides our users with an effective, easy-to-use way to enhance their English writing and generate clear, concise and error-free English language content. Our solutions involve Natural Language Processing, or NLP technology, involving rule-based and statistical algorithms, which are used by our software to scan thousands of user-generated text passages and user emails regularly to “learn” the way the human mind works in the process of writing. As a result, our software goes beyond providing relevant grammatical and typographical corrections, but also improves the style, tone and clarity of our users’ writing. Our English writing software solutions are built in a flexible proprietary software program that is deployable on Mac-based and Windows-based personal computers.
The Super-Sized Network Security Mastery Bundle for $69
DO YOU LIKE WHAT YOU’VE READ?Join our subscription list and receive our content right in your mailbox. If you like to receive some Great deals our Freebies then subscribe now! Name Email
read moreGoSafe 535 1296p Super Wide Angle Dash Cam for $109
DO YOU LIKE WHAT YOU’VE READ?Join our subscription list and receive our content right in your mailbox. If you like to receive some Great deals our Freebies then subscribe now! Name Email
read more
Quickly Transform Vectors or Text into Realistic Sketches with Super Sketch – only $9!
NOW ON: Quickly Transform Vectors or Text into Realistic Sketches with Super Sketch – only $9!
Expires: March 7, 2018, 11:59 pm EST

Have trouble sketching out a stick figure? Not to worry. Even for the least artistic designers out there, you can achieve results with Super Sketch! This amazing Photoshop Action instantly transforms your logos, vectors and even text into a realistic sketch appearance. Simple to use, with just a few clicks you can play around with the organized layers to customize and combine the perfect sketch appearance for your designs.
Highlights:
- Easily convert your design element into a realistic sketch.
- Works on logos, vectors, text.
- Easy to use Photoshop Action.
- Fully customizable – change colors, edit lines, endless combinations.
- Hi-Res results – Landscape (3000×2000 px) and Portrait (2000×3000 px), 300 DPI.
Previews:







Pricing:
Normally, this powerful Photoshop Action sells for $15, but for a limited time only, you can get Super Sketch for only $9! That’s a 40% savings off the regular price. Or get the Extended license which allows you to use any graphics created using Super Sketch in illustrations, templates and printable items that will be resold for only $19!
Click the BUY NOW button to start sketching today!
Deal terms:
- Delivered as an instant download, after completing your purchase.
- Requires Adobe Photoshop CS3 or later.
- May be used for commercial or personal projects, for yourself or your clients.
- The Extended License is required if you wish to use any graphics created using Super Sketch in illustrations, templates and printable items that will be resold (such as prints, t-shirts, mugs, stickers).
- Cannot be sublicensed, resold, shared, transferred, or otherwise redistributed on its own.
Easily Erase Objects with Super Eraser Pro for Mac – only $9!
DO YOU LIKE WHAT YOU’VE READ?Join our subscription list and receive our content right in your mailbox. If you like to receive some Great deals our Freebies then subscribe now! Name Email
read moreIT Security Specialist Super Bundle for $59
DO YOU LIKE WHAT YOU’VE READ?Join our subscription list and receive our content right in your mailbox. If you like to receive some Great deals our Freebies then subscribe now! Name Email
read moreMarvel Licensed RC Super Drones for $82
DO YOU LIKE WHAT YOU’VE READ?Join our subscription list and receive our content right in your mailbox. If you like to receive some Great deals our Freebies then subscribe now! Name Email
read moreThe Super-Sized Ethical Hacking Bundle for $43
DO YOU LIKE WHAT YOU’VE READ?Join our subscription list and receive our content right in your mailbox. If you like to receive some Great deals our Freebies then subscribe now! Name Email
read more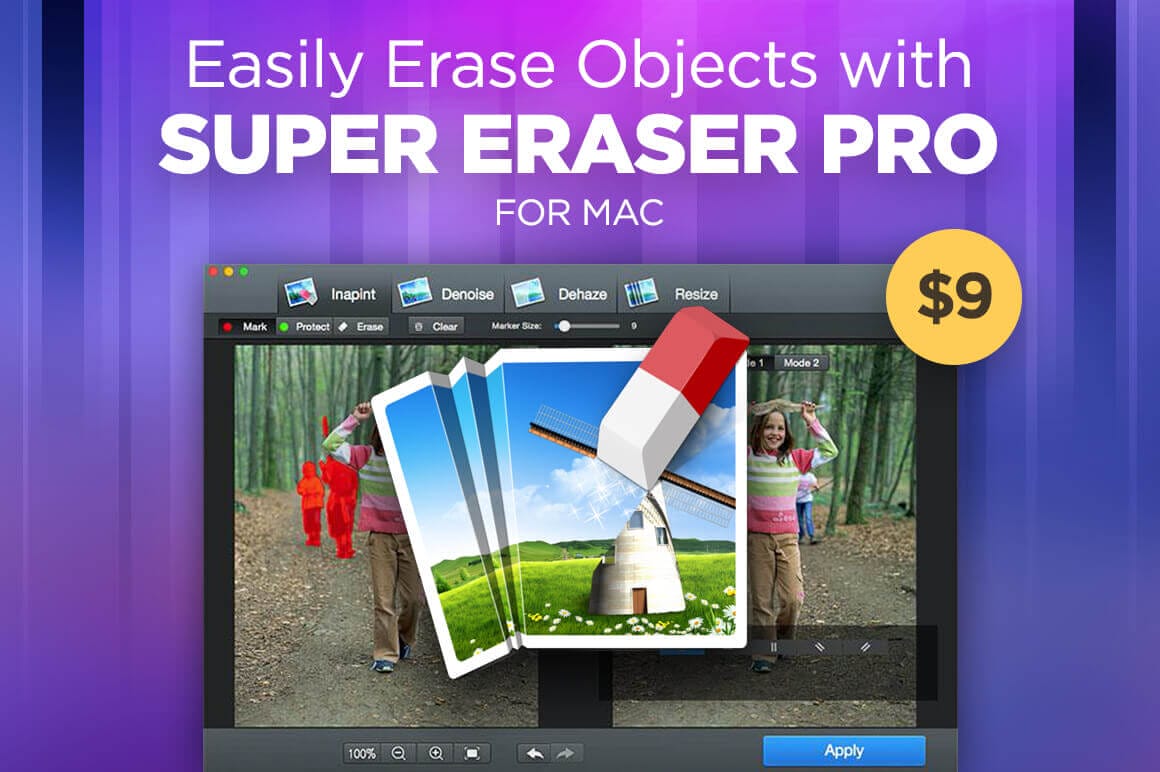
Easily Erase Objects with Super Eraser Pro for Mac – only $9!
NOW ON: Easily Erase Objects with Super Eraser Pro for Mac – only $9!
Expires: January 10, 2018, 10:59 pm EST

It’s time to turn your mouse into a magic wand. With Super Eraser Pro for Mac, you’ll find yourself instantly transforming your normal photos into extraordinary ones. With this quick and easy-to-use tool, you can instantly scale images and erase any unwanted objects from people to buildings to watermarks. Working with multiple file formats (JPG, PNG, GIF, BMP…), you can instantly make your changes and even preview them in real time.
Highlights:
- Instantly remove unwanted objects in a photo without losing quality.
- Erase watermarks, people, buildings, dates, etc.
- Quick and easy – work your magic with just a few clicks.
- Haze removal – create a clear vision with your image.
- Live Preview – see effect changes in real time.





Pricing:
Normally, this fabulous photo tool sells for $29.99 but for a limited time only, you can get Super Eraser Pro for Mac for just $9! That’s a savings of 70% off the regular price.
Click the BUY NOW button to start erasing today!
Deal terms:
- You will receive a setup file along with your unique license key, instantly after completing your purchase.
- System requirements: OS X 10.7 or later.
- 1 license for 1 Mac.

The Super-Sized Ethical Hacking Bundle for $25

KEY FEATURES
Did you know you can make money identifying and fixing bugs on some of the biggest web apps on earth? Last year, Facebook paid $5 million to independent hackers while Google paid over $6 million as part of their bug bounty programs. And they’re far from alone. In this course, you’ll learn how to legally hack major companies like Facebook, Google, and PayPal and get paid to do it.
- Access 72 lectures & 5.5 hours of content 24/7
- Learn how to get paid for hacking & disclosing bugs to major companies
- Get familiar w/ Burp Suite, browser plugins, & Kali Linux
- Explore types of vulnerability such as SQL, XSS, CSRF injection, & more
- Discover the methodology for performing bug bounty
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Amit Huddar is an Internet Entrepreneur and Software Engineer. He runs his own software company “Softdust,” which develops products for new technologies like wearables and other gadgets. He opted for computer science engineering in 2013 at SSIT and started his software company in his first year of engineering.
His skills include: Android app development, HTML, CSS, PHP, C, C++, JAVA, Linux, Building Custom Linux OS, Cloud Computing. Penetration testing, Kali Linux and Hacking.

KEY FEATURES
This course is targeted towards aspiring information security professionals who aren’t sure where to start. Beginning with basic security fundamentals, this course elevates through more advanced topics, ultimately providing you with the knowledge you need to pass the globally-recognized CompTIA Security+ certification exam.
- Access 67 lectures & 10.5 hours of content 24/7
- Cover basic security fundamentals, threats, & vulnerabilities
- Explore network security
- Dive into host & application security
- Discuss risk management & business continuity planning
- Study to ace the CompTIA Security+ certification exam on the first attempt
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Mohamed Atef is an ICT Consultant, Senior Penetration tester and certified instructor with more than 20 years of experience in professional and academic courses and 2 books published.
- Certified Information System Security Professional (CISSP) ID #517943
- Microsoft Certified Trainer (MCT) ID #3022752
- EC Council Certified Instructor (CEI) ID #ECC51750391761
- CEH: Certified Ethical Hacking ID #ECC64515022319
- Certified Cisco System Instructor (CCSI)
- Microsoft Certified System Engineer (MCSE)
- Microsoft Certified IT Professional (Windows Server Administration 2008)
- CompTIA Certified (Network +) ID #
- CompTIA Certified (Server +)
- CompTIA Certified (Linux +)
- CompTIA Certified (Security +)
- Cisco Certified Network Associate (CCNA)ID #CSCO11273248
- Cisco Certified Network Professional (CCNP)
- Project Management Professional (PMP) )ID #1772374

KEY FEATURES
To break into the world of professional penetration testing, you’ll need to be an ace with Kali Linux. This course will introduce you to the latest ethical hacking tools and techniques with Kali Linux, using a testing lab for practicing different types of attacks. Across the course, you’ll simulate an entire penetration test from beginning to end, giving you verifiable hands-on experience.
- Access 80 lectures & 8.5 hours of content 24/7
- Get comfortable w/ Kali Linux & learn the penetration testing phases
- Manage Kali Linux HTTP & SSH services
- Discover essential tools like Netcat & WireShark
- Gather passive & active information
- Explore how to perform & defend against a variety of attacks
- Receive monthly virtual machines as a hacking challenge
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Mohamed Atef is an ICT Consultant, Senior Penetration tester and certified instructor with more than 20 years of experience in professional and academic courses and 2 books published.
- Certified Information System Security Professional (CISSP) ID #517943
- Microsoft Certified Trainer (MCT) ID #3022752
- EC Council Certified Instructor (CEI) ID #ECC51750391761
- CEH: Certified Ethical Hacking ID #ECC64515022319
- Certified Cisco System Instructor (CCSI)
- Microsoft Certified System Engineer (MCSE)
- Microsoft Certified IT Professional (Windows Server Administration 2008)
- CompTIA Certified (Network +) ID #
- CompTIA Certified (Server +)
- CompTIA Certified (Linux +)
- CompTIA Certified (Security +)
- Cisco Certified Network Associate (CCNA)ID #CSCO11273248
- Cisco Certified Network Professional (CCNP)
- Project Management Professional (PMP) )ID #1772374

KEY FEATURES
You hear about it all the time: companies getting hacked, having their websites shut down or their customers’ data compromised. When that happens, it’s time to call in ethical hackers to break into network systems, evaluate their security, and propose solutions. After this course you’ll be well on your way to being one of these hackers, paid generously to hack networks, apps, emails, social media accounts, and more!
- Access 89 lectures & 16 hours of content 24/7
- Understand how to bypass different security layers after getting proper approval
- Learn how to compromise computers, crack passwords, crash systems & compromise applications
- Run a buffer overflow from scratch
- Stride towards a career in this fast-growing IT profession
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Mohamed Atef is an ICT Consultant, Senior Penetration tester and certified instructor with more than 20 years of experience in professional and academic courses and 2 books published.
- Certified Information System Security Professional (CISSP) ID #517943
- Microsoft Certified Trainer (MCT) ID #3022752
- EC Council Certified Instructor (CEI) ID #ECC51750391761
- CEH: Certified Ethical Hacking ID #ECC64515022319
- Certified Cisco System Instructor (CCSI)
- Microsoft Certified System Engineer (MCSE)
- Microsoft Certified IT Professional (Windows Server Administration 2008)
- CompTIA Certified (Network +) ID #
- CompTIA Certified (Server +)
- CompTIA Certified (Linux +)
- CompTIA Certified (Security +)
- Cisco Certified Network Associate (CCNA)ID #CSCO11273248
- Cisco Certified Network Professional (CCNP)
- Project Management Professional (PMP) )ID #1772374

KEY FEATURES
In this course you’ll start with the basics of social engineering and elevate to an advanced enough level to be able to hack into all major operating systems, generate different types of Trojans, and deliver them using smart social engineering practices. Focused on the practical side of penetration testing, you’ll first set up a lab before getting real practice with penetration testing that will help you build a career and protect yourself from malicious hacking.
- Access 105 lectures & 11.5 hours of content 24/7
- Learn how to gather information about your target
- Generate evil files like backdoors, keyloggers, credential harvesters, & more for Windows, macOS, & Linux
- Discover a number of social engineering methods to deliver Trojans to a target like creating fake websites
- Interact w/ the systems you’ve compromised by accessing the file system, escalating your privileges, & more
- Learn how to protect yourself & your systems from these attacks
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Zaid Al-Quraishi is an ethical hacker, pentester, and programmer. He has extensive experience in ethical hacking and penetration testing, more specifically with regard to network security. Zaid started making video tutorials in 2009 for the ethical hacking website iSecuri1ty, and has also served as an editor, manager, and penetration tester for the company. He teaches mostly by example, specifically by first explaining the theory of each technique and then how it translates to a real-life situation.

KEY FEATURES
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. As you gain a complex understanding of websites, you will then learn how you can exploit them to carry out a number of powerful cyber attacks. You’ll track from a beginning to advanced level and by the time you finish you’ll be able to launch attacks and test the security of websites and apps the same way that black hat hackers would, and be able to fix these vulnerabilities.
- Access 93 lectures & 9 hours of content 24/7
- Learn how to gather information about your target site like discovering the DNS server used & subdomains
- Discover, exploit, & fix a number of vulnerabilities like file upload, code execution, SQL injection, XSS, & much more
- Understand what you can do w/ the access gained from vulnerabilities
- Explore the basic exploitation of attacks & the advanced methods to enhance them
- Learn how & why vulnerabilities are exploitable, how to fix them, & the right practices to avoid them
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Zaid Al-Quraishi is an ethical hacker, pentester, and programmer. He has extensive experience in ethical hacking and penetration testing, more specifically with regard to network security. Zaid started making video tutorials in 2009 for the ethical hacking website iSecuri1ty, and has also served as an editor, manager, and penetration tester for the company. He teaches mostly by example, specifically by first explaining the theory of each technique and then how it translates to a real-life situation.

KEY FEATURES
This course allows you to follow, in real time, each stage of a penetration testing engagement so you cna tweak and train your skills over and over again. You’ll get the latest tools and techniques using Rapid 7’s tool Metasploit to exploit targets, as well as run post exploitation techniques and utilize PowerShell with Empire. By giving you interactive, hands-on experience, you’ll be able to learn more efficiently and build a lucrative career as a penetration tester.
- Access 23 lectures & 3 hours of content 24/7
- Understand how to move around Metasploit
- Learn how to not be seen by intrusion detection system & evade anti-virus software used by professional penetration testers
- Explore Empire, how to gain sessions known as “agents,” escalate privileges & migrate over to the Metasploit framework
- Discover penetration tactics in real-time through visual learning
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Nick Smith has substantial experience in Networking & Systems Management covering Windows, *nix & Mac. He has worked from the ground up as a Systems Administrator / Network Administrator, ISP, Provisioning Broadband services & MPLS Networks in large corporate environments. He has been involved in running penetration test engagements within the Financial Sector Services for some of the largest global banking Institutes. Nick currently holds the Qualys Vulnerability Assessor Certification, & will explore CREST and others when he has time in the future.

KEY FEATURES
This course will give you an in-depth look into WiFi hacking and security. By course’s end, regardless of experience, you’ll be confident breaking all types of WiFi encryption methods and be ready to start pursuing a career in network security.
- Access 21 lectures & 3 hours of content 24/7
- Learn how to properly prepare your working environment
- Explore some basics about networks & how they work
- Discover every possible attack you can perform on a target network without being connected to it
- Crack & bypass security mechanisms of a network
- Understand how to anonymously stay on the network without being noticed
- Reduce the risk of being hacked by learning to secure your network
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
LearnPentest is a group of penetration testers and ethical hackers with an extensive background in web application security, web and software development, network administration and exploit development. They have over 7 years of professional experience in the cyber security domain. Their instructors hold some of the most valuable certifications in the cyber security domain including: OSCP, LPT, C|EH, CISSP, OSCE.

KEY FEATURES
Internet security has never been as important as it is today with more information than ever being handled digitally around the globe. In the first course of this four volume bundle, you’ll get an introduction to hacking and how to protect yourself and others. You’ll develop an understanding of the threat and vulnerability landscape through threat modeling and risk assessments, and build a foundation for which to expand your security knowledge.
- Access 117 lectures & 11 hours of content 24/7
- Explore the Darknet, malware, exploit kits, phishing, zero day vulnerabilities, & more
- Learn about global tracking & hacking infrastructures that nation states run
- Understand the foundations of operating system security & privacy functionality
- Get a crash course on encryption, how it can be bypassed, & what you can do to mitigate risks
- Discover defenses against phishing, SMShing, vishing, identity theft, & other cons
PRODUCT SPECS
Details & Requirements
- Length of time users can access this course: lifetime
- Access options: web streaming, mobile streaming
- Certification of completion not included
- Redemption deadline: redeem your code within 30 days of purchase
- Experience level required: all levels
Compatibility
- Internet required
THE EXPERT
Nathan House has over 24 years experience in cyber security where he has advised some of largest companies in the world, assuring security on multi-million and multi-billion pound projects. He is CEO of Station X, a cyber security consultancy. More recently Nathan acted as the lead security consultant on a number of the UK’s mobile banking and payment solutions helping secure to date over £71Bn in transactions.
His clients have included; BP, ExxonMobil, Shell, Vodafone, VISA, T-mobile, GSK, COOP Banking Group, Royal Bank of Scotland, Natwest, Yorkshire bank, BG Group, BT, London 2012.
Over the years he has spoken at a number of security conferences, developed free security tools, and discovered serious security vulnerabilities in leading applications. Nathan’s qualifications and education include:
- BSc. (Hons) Computing ‘Networks & Communication’ 1st Class Honors
- SCF : SABSA Charted Architect Foundation
- CISSP : Certified Information Systems Security Professional
- CISA : Certified Information Systems Auditor
- CISM : Certified Information Security Manager
- ISO 27001 Certified ISMS Lead Auditor
- CEH : Certified Ethical Hacker
- OSCP : Offensive Security Certified Professional
